This is an article I have been meaning to do for some time and discusses the odd occurrence where if the first sector a WD MyBook external hard drive fails the decryption does not engage and the drive becomes unreadable. While there are off the shelf tools to perform decryption I will be using open source software to solve this problem. I don’t want to get into a discussion about which tools I have used but for those that are interested see the following link.
Most WD 3.5 inch MYBOOK essentials have their data encrypted to provide security should your drive go missing. This can create issues when data recovery is necessary.

After we disassemble the enclosure we are left with the hard drive below left and the usb – sata PCB BRIDGE, see below right.

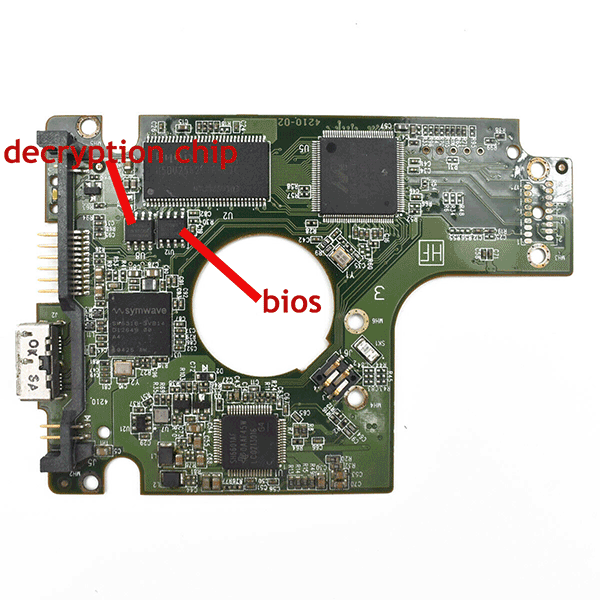
Highlighted on the USB-SATA bridge is a chip the sole purpose of which is to scramble/encrypt the data written to the hard drive. So if we were to plug in the drive to a computer without the bridge the drive would appear as empty and devoid of data. The first sector on any hard drive contains information about the number of partitions on that drive and their location. Should this sector fail then the decryption fails to engage and the drive remains encrypted but unreadable.
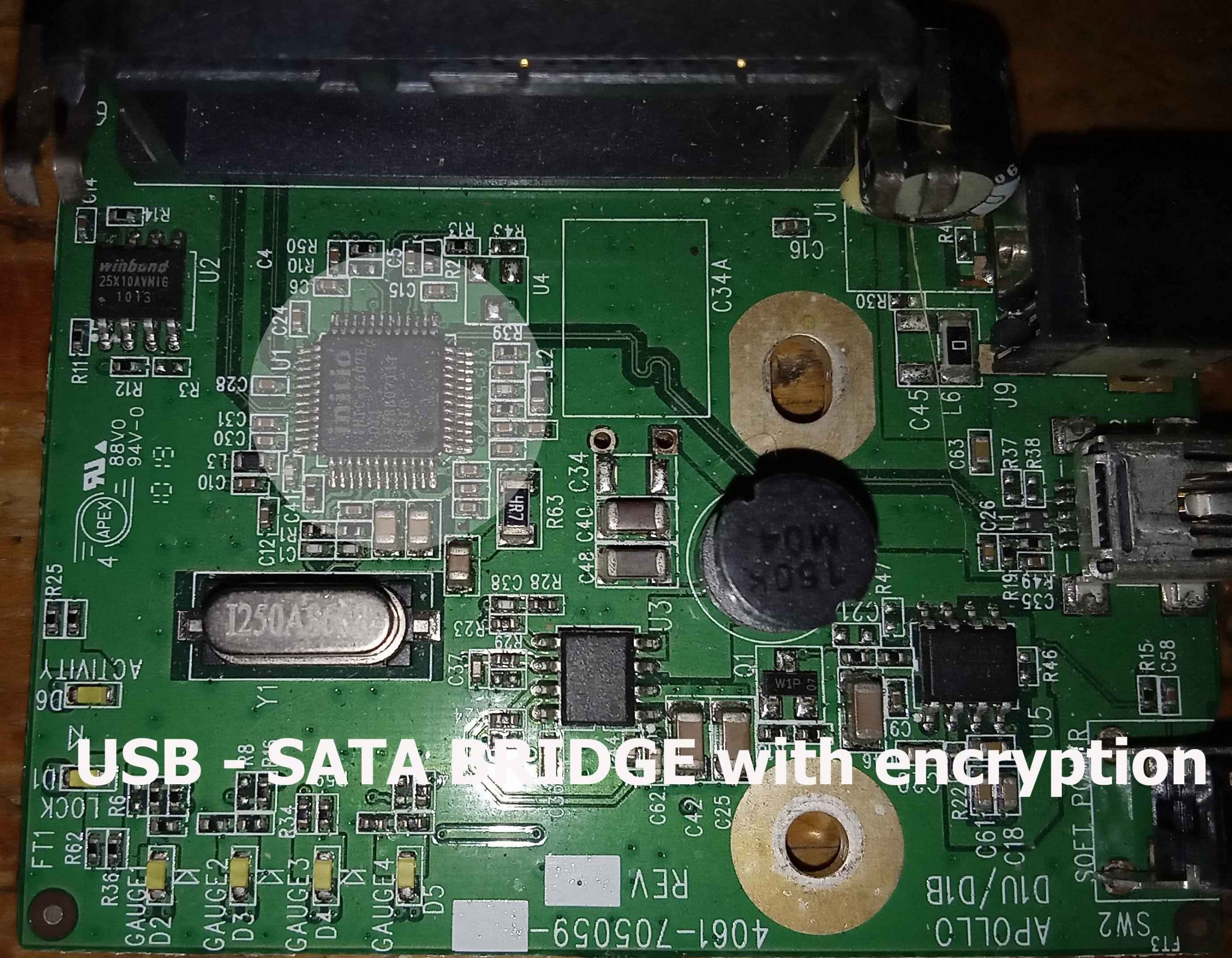
For the purposes of this article I will be using a more modern WD MY Passport portable see picture below left. The drive’s electronics , see middle picture below, has the encryption chip soldered to the printed circuit board and I have replaced this PCB with equivalent electronics with a sata interface and no encryption. This then for the purposes of our discussion is an exact analog of the WD MY Book.
Before we get further in I need to acknowledge the author of the document contained in this link
Now to decrypt the drive we need to obtain the disk encryption key or DEK and this located at a specific sector on the hard drive and this location changes depending on the type of encryption chip.
JMicron JMS538S chip
500 GB 976769056
750 GB 1465143328
1 TB 1953519648
1.5 TB 2930272288 *
2 TB 3907024928
3 TB 5860528160
4 TB 7814031392
Symwave SW6316 chip
500 GB 976770435
750 GB 1465144707
1 TB 1953521027
1.5 TB 2930273667 *
2 TB 3907026307
3 TB 5860529539
4 TB 7814032771 *
If all of this is starting to look complicated then would be right but this is where another free tools saves the day.
REALLYMINE is a program that decrypts the encrypted WD hard drives. It will in fact decrypt the whole drive automatically however it is slow and will fall over when it tries to read bad sectors which makes it unusable with drives that have bad sectors.
It does however have a great tool which not only gives us the DEK it also informs us of the encryption type used.
We can see in the picture it delivers the DEK and the fact the drive as a SYMWAVE encryption chip.
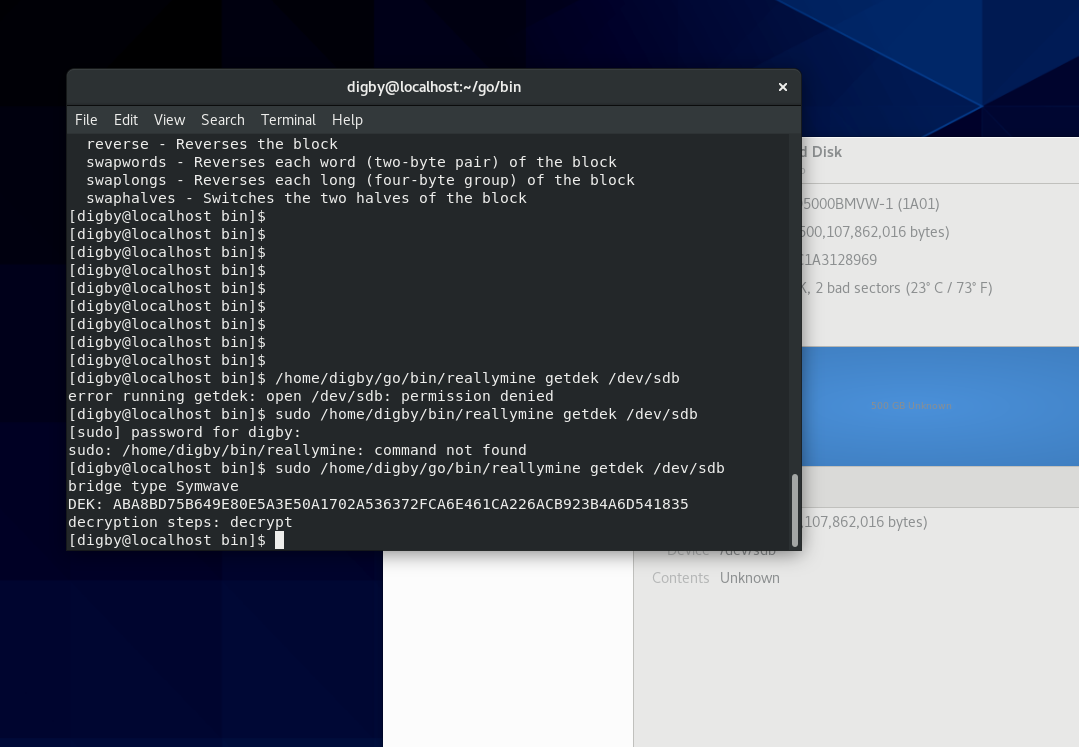
Now that we have the DEK, we can set up the encryption filter. In my example, the drive was at /dev/sdb
So the following filter can implemented in BASH under linux , in the following command I have placed the DEK in the file dek.hex.
cat dek.hex | xxd -p -r | sudo cryptsetup -d – –hash=plain \
–key-size=256 -c aes-ecb create wd /dev/sdb
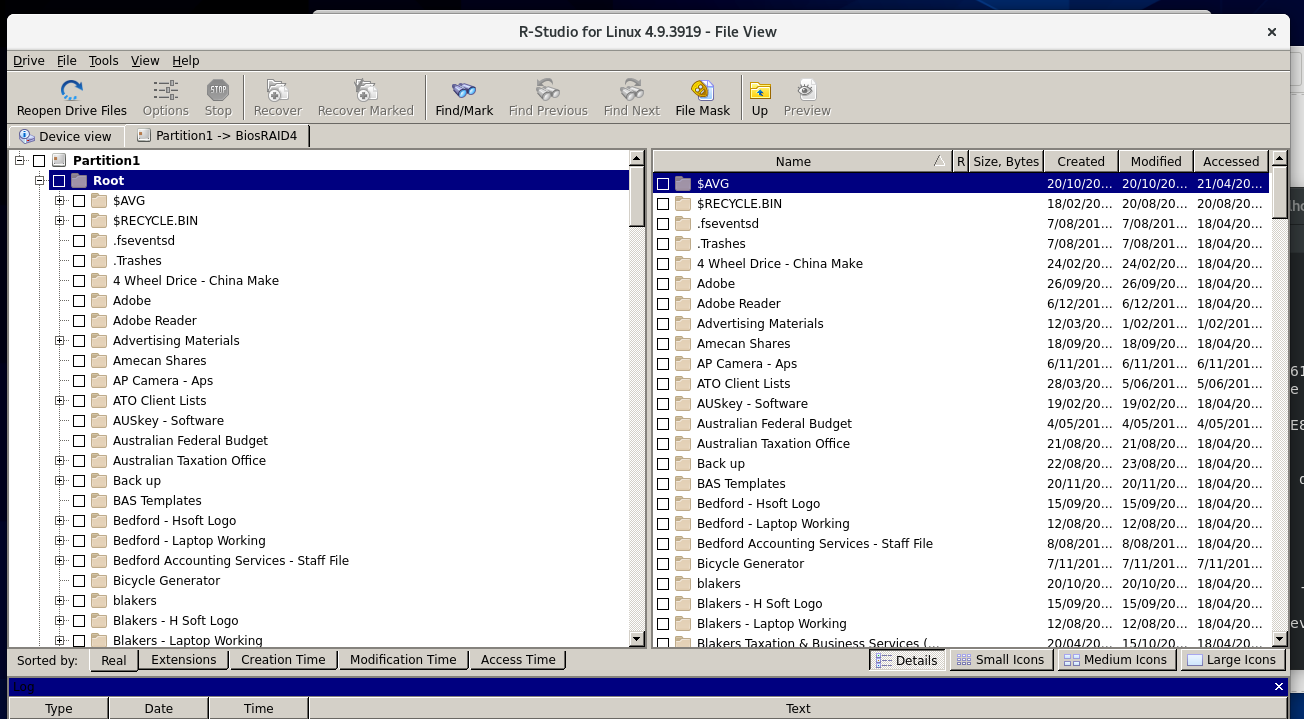
With our filter in place the drive is automatically decrypted and we can see the results in the picture below. I am using R-STUDIO to read the drive as it handles the NTFS better than Linux. WE could then using RSTUDIO extract the files to another drive or location.
Given we are possibly working with drives with bad sectors it may be you will need to make an image of this drive in which case DDRESCUE is the answer. The cloning of the drive with applied filter will also mean the clone is decrypted.
Some of our Reviews
REQUEST A QUOTE
Address
126 Whatley Crescent Maylands
call:(08) 6180 6959
126 Whatley Crescent
6 Days a week from 8:00am – 5:00pm