I am increasingly seeing laptops that were purchased in the last 18 months that have been bitlocker enabled but the owners were unaware of this nor did they have the RECOVERY ID. This is a major problem should anything go wrong and data recovery is required.
How could this possibly happen?
Well If the following requirements are met on a new laptop
- BIOS must be in Unified Extensible Firmware Interface (UEFI) mode
- Trusted Platform Module (TPM) or Platform Trust Technology (PTT) is enabled
- SecureBoot is enabled
- solid-state storage (SSD or eMMC)
- nonremovable (soldered) RAM.
- Core isolation is enabled in Microsoft Windows 10 , 11
- Modern Standby Spec
Then your drive will be bitlocker encrypted automatically.
According to Microsoft automatic device encryption only starts after the Out-Of-Box Experience (OOBE) is completed and a Microsoft Account (MSA) is used on the system (e.g. use MSA for Windows login, add MSA as email, app, and work or school account, log in to the Microsoft Store app with MSA, redeem or activate Microsoft Office or other Microsoft applications with MSA).
So how is it the owners of these laptops did not know the computers were bitlocker encrypted and that a Recovery ID would be needed to recover their important. Data. Well in both cases a Lenovo Laptop and 2 HP Laptops were setup by 3rd parties. Both supplier and purchaser of the laptops were unaware of the bitlocker activation nor did they know of the recovery key.
Because bitlocker activation is automatic and the boot up process never asks for a recovery ID the parties were unaware that their drives were bitlocker encrypted.
Below lists when Dell Laptops will be automatically Bitlocker Encrypted.
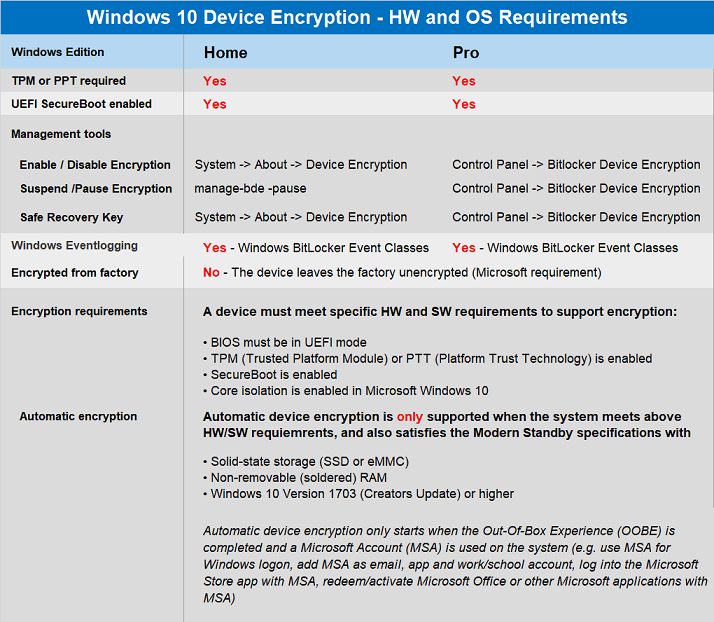
Bit Locker Boot Process
TPM, operating system drives that are BitLocker-protected can be unlocked in four ways:
- TPM-only.Using TPM-only validation does not require any interaction with the user to unlock and provide access to the drive. If the TPM validation succeeds, the user sign in experience is the same as a standard logon..
- TPM with startup key.In addition to the protection that the TPM-only provides, part of the encryption key is stored on a USB flash drive, referred to as a startup key.
- TPM with PIN.In addition to the protection that the TPM provides, BitLocker requires that the user enter a PIN. Data on the encrypted volume cannot be accessed without entering the PIN.
- TPM with startup key and PIN.
Automatic Bitlocker encryption usually uses the first method
How the Bitlocker Boot Process can become corrupt
If the TPM is missing or changed or if BitLocker detects changes to the BIOS or UEFI code or configuration, critical operating system startup files, or the boot configuration, BitLocker enters recovery mode, and the user must enter a recovery password to regain access to the data
Because the recovery id is contained within the laptops TPM module and that the Recovery ID is not asked for when the laptop boots end users are unaware of Bitlocker as it was setup by a 3rd party.
It is also for a bios update to affect the TPM data.
.
It is also possible to corrupt the Boot Process , eg power outages so that the encrypted drive’s file system becomes corrupted and cannot be fixed by the Start Up Repair Process without the Recovery ID.
How to Backup your Bitlocker Recovery Id
To start, Press Start Key + R the BitLocker Drive Encryption control panel.
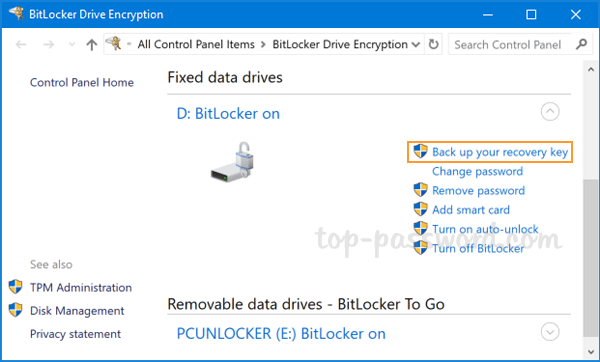
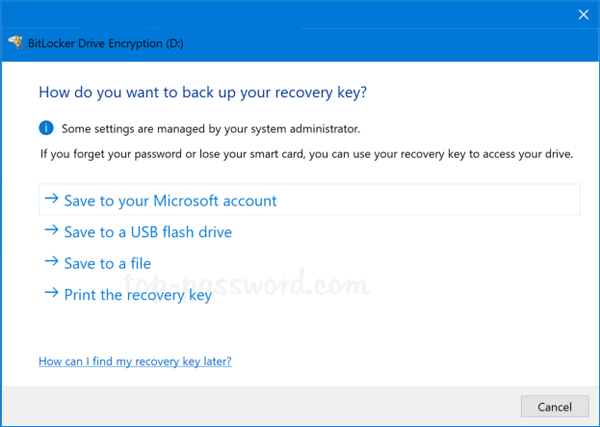
DISABLE BITLOCKER ENCRYPTION
It is also possible to disable the Bitlocker encryption.
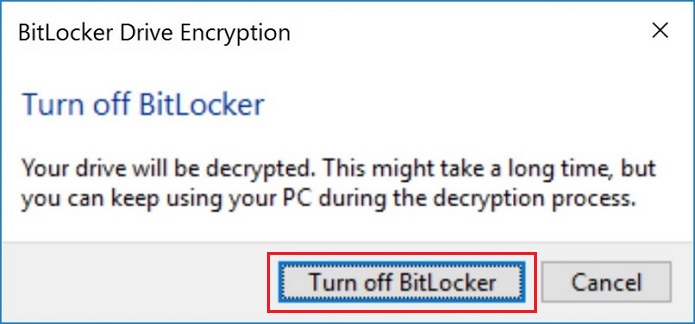
It cannot be emphasized enough if you do not back up your data or know your Recovery ID data recovery is not possible.
References
https://hardsoft-support.kayako.com/article/99-windows-10-bitlocker-turns-on-without-a-notice
https://frameboxxindore.com/windows/is-bitlocker-automatically-on-windows-10.html
REQUEST A QUOTE
Address
126 Whatley Crescent Maylands
call:(08) 6180 6959
126 Whatley Crescent
6 Days a week from 8:00am - 5:00pm
